Passwords are not safe, companies should shift to AI & ML alternatives, say WEF report
A report published by the World Economic Forum (WEF), in January this year, claims that discarding the use of passwords […]
By Sectors
Protect mobile apps from threats and vulnerabilities.
Safeguard digital content from piracy and leaks.
DoveRunner vs. Competitors
Complete Security for Mobile Apps & Content
Protect apps from fraud and hacking.
Secure content from piracy and leaks.
Supported DRM
Secure content from piracy and leaks.
DoveRunner vs. Competitors
Resources Library
Blogs: Insights, trends, and updates on security.
White Papers: In-depth research on security solutions.
Webinars: Expert discussions on security challenges.
Case Studies: Real-world solutions for security threats.
Events & Conferences: Industry networking and security trends.
Get detailed mobile app and content security reports.
Feature breakdowns and technical specifications of our solutions.
Step-by-step checklists to help you stay security-ready.
Latest announcements and milestones from our organization.
Expert conversations on mobile app security, live streaming security and real-world defence strategies.
Featured Resources
Bahrain, officially called the Kingdom of Bahrain, is an island

All modern devices maintain hyperconnection because they enable essential data

Developers Resources
Featured Resources
Bahrain, officially called the Kingdom of Bahrain, is an island

All modern devices maintain hyperconnection because they enable essential data

About DoveRunner
Featured Resources
Bahrain, officially called the Kingdom of Bahrain, is an island

All modern devices maintain hyperconnection because they enable essential data

A report published by the World Economic Forum (WEF), in January this year, claims that discarding the use of passwords […]
Security vulnerabilities in Android OS have been long exploited by hackers to their advantage, resulting in wide-ranging mayhem and business
The last year witnessed a huge surge in cyberattacks, both on individuals and big companies. With a growing dependence on
Hackers are constantly on the prowl to find their next victim. It is not only unsuspecting individuals who become their
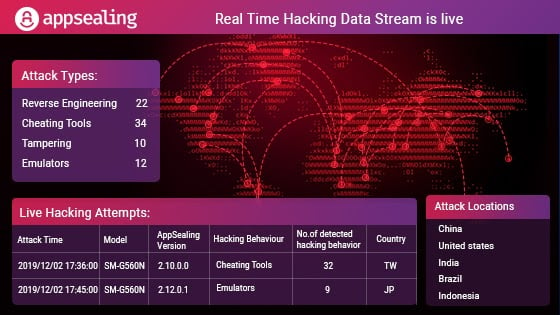
With a lot of research, testing and development over the months, we are pleased to announce our Real-time hacking Data
Google recently announced the release of Android Q on September 3rd and was rebranded to Android 10 to make easy for