Rooting and jailbreaking aren’t new concepts—they’ve been around for years as ways for tech-savvy users to customize their devices and break free from manufacturer restrictions. And while companies like Google and Apple have responded by loosening some restrictions and tightening security, these practices haven’t gone away. They’ve just evolved. What we’re seeing now is that rooted and jailbroken devices, though relatively rare, pose an outsized security threat to businesses.
The numbers tell a concerning story: our analysis reveals that rooted devices are more than 3.5 times more likely to be hit with mobile malware compared to standard devices. Even more worrying, the vulnerabilities these modified devices introduce can become gateways for attackers to infiltrate entire organizations—whether through careless mistakes or as part of deliberate, sophisticated attacks.
In this blog, we’ll walk you through:
- Why rooting and jailbreaking still matter for enterprise security
- The landscape of current rooting tools and how they’re getting more sophisticated
- How developer communities are constantly adapting to stay ahead of security measures
- Real data that shows just how much risk these devices actually pose
The Current State of Mobile Device Rooting
Understanding Rooting vs Jailbreaking
Rooting is essentially hacking your own Android device to gain administrator-level access—think of it like getting “superuser” permissions on Linux or macOS. With root access, users can tweak system files, install apps that normally wouldn’t be allowed, and remove those annoying carrier or manufacturer restrictions. For tech enthusiasts, it’s about taking full control. For security professionals, it’s a red flag because it also means someone with malicious intent could reverse engineer your company’s apps.
Jailbreaking is the iPhone version of rooting, though it goes a bit further. It’s not just about admin access—jailbreaking lets you bypass Apple’s notoriously locked-down bootloader, install apps from outside the App Store (something called “sideloading”), and fundamentally change how iOS operates. The key difference? Android already lets you sideload apps without rooting, but on iOS, you need to jailbreak first.
Here’s the thing: while these might seem like harmless tweaks to gain more control over a personal device, rooted and jailbroken devices behave very differently from regular ones when it comes to security—and not in a good way.
Data Insights: The Real Risk Profile
How Common Are Rooted Devices, Really?
Looking at enterprise environments, we’re seeing rooted devices make up about 0.1% of all mobile devices. That might sound tiny—and it is—but here’s where it gets interesting. That small percentage is responsible for a disproportionate amount of security headaches.
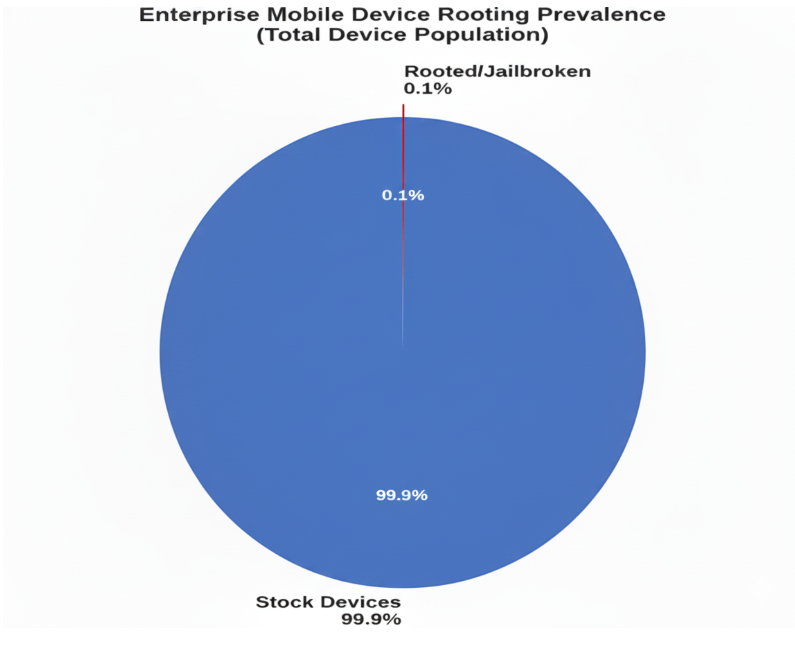
Figure 1: Enterprise Mobile Device Rooting Prevalence
Breaking this down by platform:
- Android: 1 in 400 devices (0.25%) is rooted
- iOS: 1 in 2,500 devices (0.04%) is jailbroken
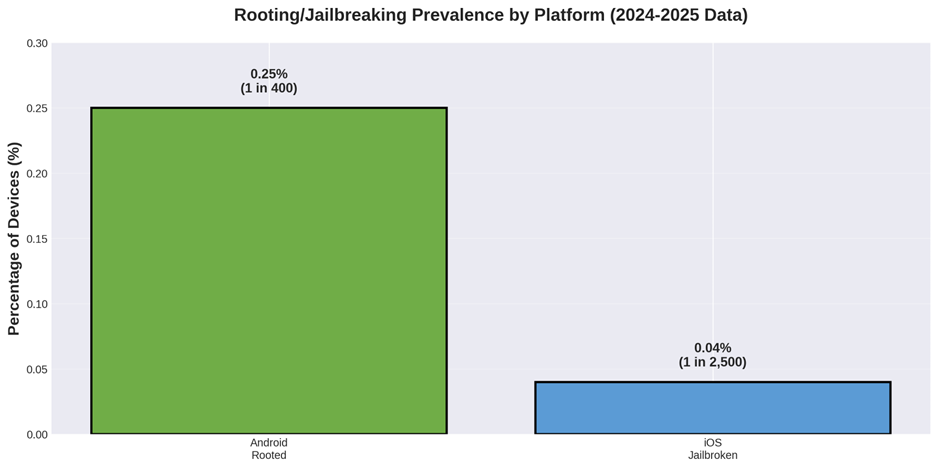
Figure 2: Rooting/Jailbreaking Prevalence by Platform (2024-2025)
Risk Exposure Comparison
The security implications of rooted devices become crystal clear when we compare threat exposure between standard and modified devices. Our 12-month analysis reveals some eye-opening patterns.
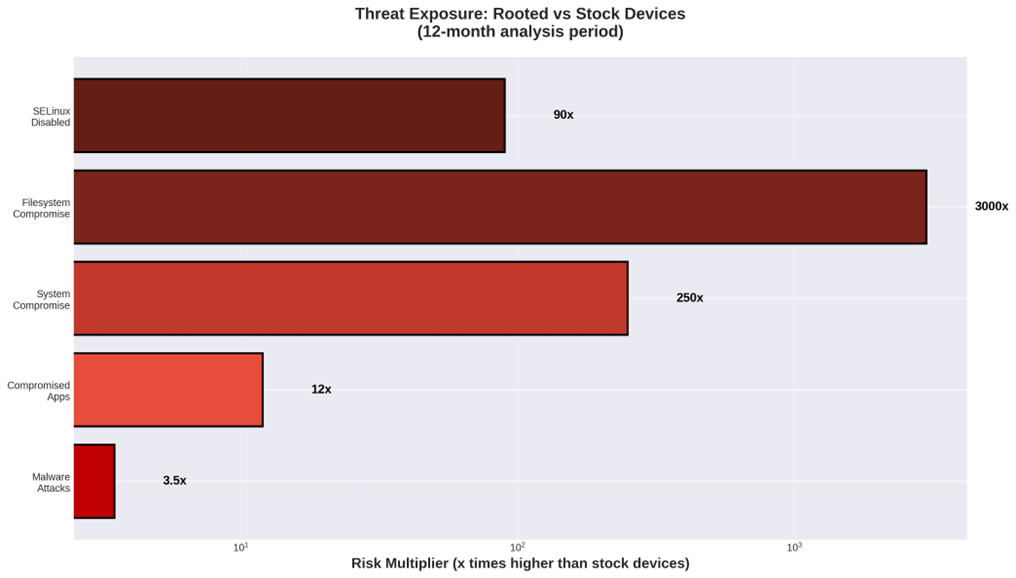
Figure 3: Threat Exposure – Rooted vs Stock Devices (12-month analysis)
According to our data, the exposure factor of rooted devices versus stock devices varies from 3x to ~3,000x, meaning rooted devices are substantially more vulnerable to threats.
Let’s break that down:
Detection Trends: The Rising Threat
Our detection data throughout 2024 reveals some concerning trends. We’re not just seeing steady numbers—we’re watching certain rooting tools gain serious momentum.
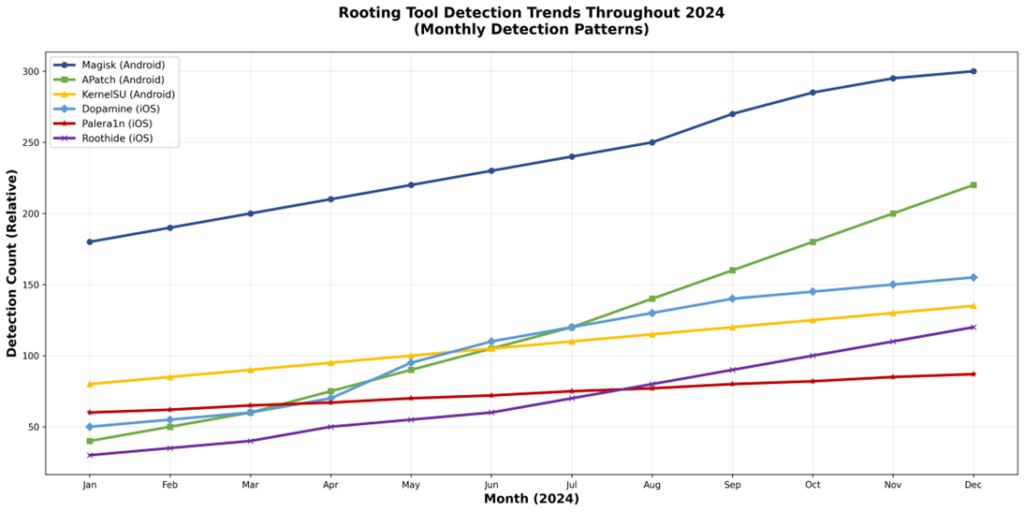
Figure 4: Rooting Tool Detection Trends Throughout 2024
For some rooting tools—particularly APatch, Magisk, and Dopamine—we’ve seen a clear ramp-up in detections in recent months. This upward trend tells us something important: these threats aren’t going away. If anything, they’re becoming more prevalent.
Key observations:
- Android tools show consistent growth, with APatch demonstrating the steepest adoption curve
- iOS tools show periodic spikes that line up with new iOS version releases
- Overall trend is upward across all major frameworks—this isn’t a problem that’s solving itself
Developer Community Activity and Innovation Patterns
The rooting and jailbreaking ecosystem isn’t some small group of hobbyists anymore. It’s a massive, global development effort with contributors from all over the world constantly pushing out improvements and new techniques.
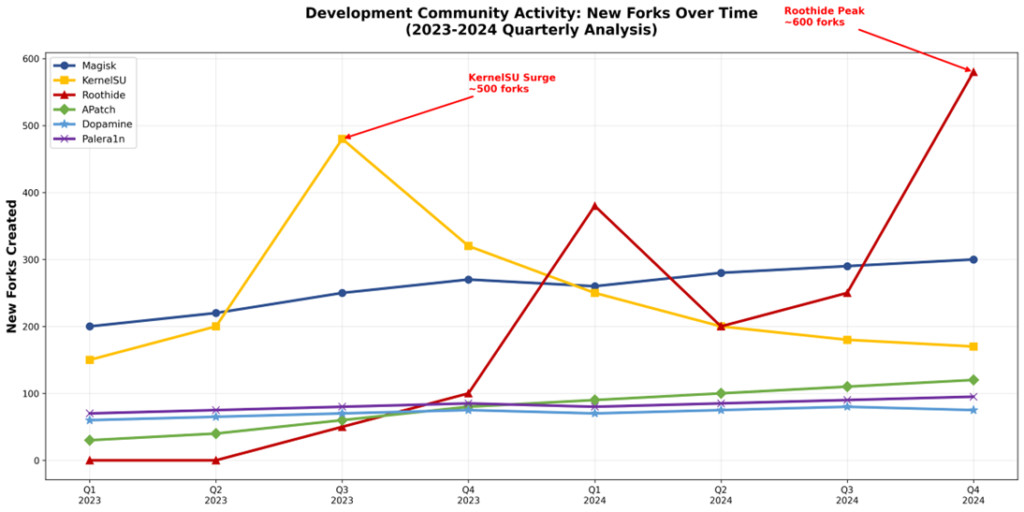
Figure 5: Development Community Activity – New Forks Over Time (2023-2024)
What the data shows:
- Magisk: Steady as they come—150-300 new forks every month
- KernelSU: Massive spike of nearly 500 forks in mid-2023
- Roothide: Two big waves—400 forks in early 2024, then a huge surge to 600 in late 2024
- APatch, Dopamine, Palera1n: Consistent activity at 50-100 new forks monthly
Here’s what’s really interesting: those sudden spikes aren’t random. They typically line up with major Android or iOS security updates. Google or Apple rolls out new protections, and within weeks, the development community mobilizes to work around them. It’s a constant back-and-forth.
Advanced Detection: Identifying Specific Rooting Tools
Detecting whether a device is rooted is one thing. Figuring out exactly which rooting tool someone used? That’s a whole different challenge. But it’s crucial information because different tools have different capabilities and different risks.
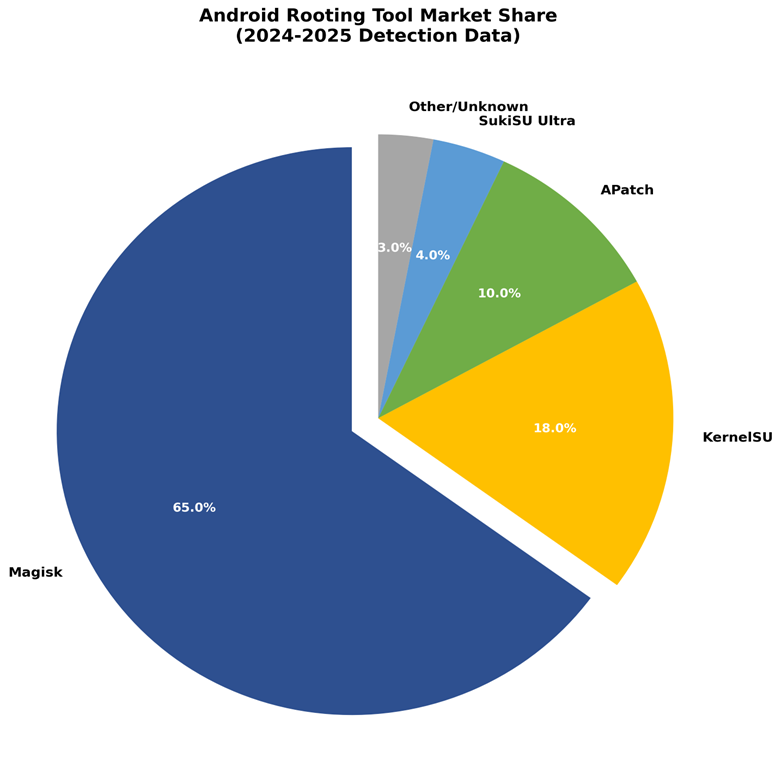
Figure 6: Android Rooting Tool Market Share (2024-2025)
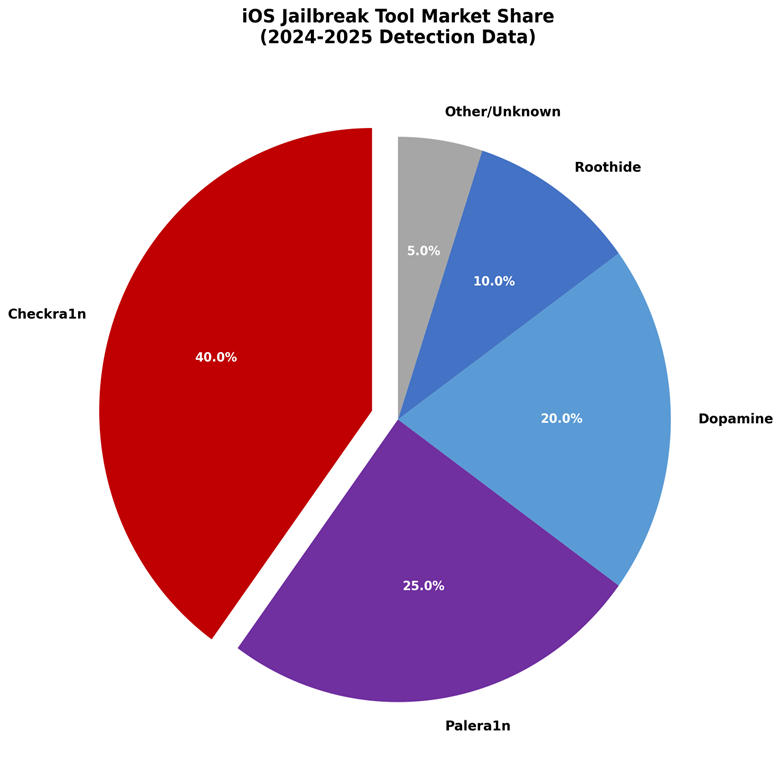
Figure 7: iOS Jailbreak Tool Market Share (2024-2025)
Despite the ongoing cat-and-mouse game between security tools and rooting frameworks, successful analysis can map out the unique footprints each tool leaves behind. This lets us identify not just that a device has been modified, but exactly how it was done.
Conclusion
Rooting and jailbreaking aren’t going anywhere. These practices continue to grant users privileged access to their device’s operating system, and that continues to open the door to malware infections, compromised apps, and full system takeovers. A single compromised device really can serve as the entry point for a much larger attack that puts an entire organization at risk.
What makes this challenge particularly pressing is how quickly rooting tools evolve. This isn’t a static threat you can solve once and forget about. Tools like Magisk, APatch, KernelSU, Dopamine, Checkra1n, Palera1n, and Roothide are constantly being updated, with new versions and techniques emerging regularly to bypass whatever security measures get put in place.
Key Takeaways:
- Rooted devices are 3.5x to 3,000x more vulnerable than stock devices
- Only 0.1% of devices are rooted, but they represent disproportionate risk
- Development activity is accelerating, with hundreds of new forks monthly
- Detection evasion is advancing, requiring sophisticated countermeasures
- Enterprise impact is severe, from malware to data exfiltration
The mobile security landscape demands constant adaptation. Organizations need to invest in advanced detection capabilities, maintain current threat intelligence, and implement comprehensive security policies to protect against these sophisticated and evolving threats.




